在 CentOS 7 中使用 strongSwan 搭建 IKEv2 VPN
本文介绍在 CentOS 7 系统中使用 strongSwan 开源软件搭建 IKEv2 方式的 VPN 配置。
本文涉及到的各项系统及软件版本:
- 服务端系统:CentOS 7.4 64位
- 客户端系统:Windows 10 专业版,版本号 1809
- 软件:strongSwan 版本 5.7.2
一、安装 strongSwan
使用 EPEL 源安装 strongSwan,因为 EPEL 包含 strongSwan 最新版本,EPEL 更新比较快,如果系统中没有,则执行下面命令安装 EPEL 源。
1、安装 EPEL 源
yum -y install epel-release
注意,这不是必须的,你也可以使用其它源安装。
2、安装 openssl
yum -y install openssl
注意,这不是必须的,请根据实际情况调整。
3、安装 strongswan
yum -y install strongswan
注意,这是必须的。
4、设置开机启动
systemctl enable strongswan
二、创建证书
1、创建 CA 根证书
1.1 创建一个私钥:
strongswan pki --gen --outform pem > ca.key.pem
1.2 基于这个私钥自己签一个 CA 根证书:
strongswan pki --self --in ca.key.pem --dn "C=CN, O=123si, CN=123si StrongSwan CA" --ca --lifetime 3650 --outform pem > ca.cert.pem
命令参数介绍:
| 参数 | 描述 |
|---|---|
--self |
表示自签证书 |
--in |
是输入的私钥 |
--dn |
是判别名 |
C |
表示国家名,同样还有 ST 州/省名,L 地区名,STREET(全大写)街道名 |
O |
组织名称 |
CN |
友好显示的通用名 |
--ca |
表示生成 CA 根证书 |
--lifetime |
为有效期, 单位是天 |
2、创建服务器端证书
2.1 创建一个私钥:
strongswan pki --gen --outform pem > server.key.pem
2.2 用我们刚才自签的 CA 证书给自己发一个服务器证书:
# 用私钥创建公钥strongswan pki --pub --in server.key.pem --outform pem > server.pub.pem# 用刚创建的公钥,创建服务器证书strongswan pki --issue --lifetime 3650 --cacert ca.cert.pem --cakey ca.key.pem --in server.pub.pem --dn "C=CN, O=123si, CN=48.85.166.86" --san="48.85.166.86" --flag serverAuth --flag ikeIntermediate --outform pem > server.cert.pem
命令参数介绍:
--issue,--cacert和--cakey就是表明要用刚才自签的 CA 证书来签这个服务器证书。
--dn,--san,--flag是一些客户端方面的特殊要求:
- iOS 客户端要求 CN 也就是通用名必须是你的服务器的 URL 或 IP 地址;
- Windows 7 不但要求了上面,还要求必须显式说明这个服务器证书的用途(用于与服务器进行认证),
--flag serverAuth; - 非 iOS 的 Mac OS X 要求了“IP 安全网络密钥互换居间(IP Security IKE Intermediate)”这种增强型密钥用法(EKU),
--flag ikdeIntermediate; - Android 和 iOS 都要求服务器别名(serverAltName)就是服务器的 URL 或 IP 地址,
--san;
3、创建客户端证书
3.1 创建一个私钥:
strongswan pki --gen --outform pem > client.key.pem
3.2 然后用刚才自签的 CA 证书来签客户端证书:
# 用私钥创建公钥strongswan pki --pub --in client.key.pem --outform pem > client.pub.pem# 用刚创建的公钥,创建客户端证书strongswan pki --issue --lifetime 3650 --cacert ca.cert.pem --cakey ca.key.pem --in client.pub.pem --dn "C=CN, O=123si, CN=48.85.166.86" --outform pem > client.cert.pem
4、打包证书为 pkcs12
openssl pkcs12 -export -inkey client.key.pem -in client.cert.pem -name "123si StrongSwan Client Cert" -certfile ca.cert.pem -caname "123si StrongSwan CA" -out client.cert.p12
执行命令后,会提示输入两次密码,这个密码是在导入证书到其他系统时需要验证的。没有这个密码即使别人拿到了证书也没法使用。
三、安装证书
cp -r ca.key.pem /etc/strongswan/ipsec.d/private/cp -r ca.cert.pem /etc/strongswan/ipsec.d/cacerts/cp -r server.cert.pem /etc/strongswan/ipsec.d/certs/cp -r server.pub.pem /etc/strongswan/ipsec.d/certs/cp -r server.key.pem /etc/strongswan/ipsec.d/private/cp -r client.cert.pem /etc/strongswan/ipsec.d/certs/cp -r client.key.pem /etc/strongswan/ipsec.d/private/
把 CA 证书(ca.cert.pem)、客户端证书(client.cert.pem)和 .p12 证书(client.cert.p12)用 FTP 复制出来给客户端用。
四、配置 VPN
1、修改主配置文件 ipsec.conf
配置文件ipsec.conf官方介绍链接:ipsec.conf: conn Reference
编辑配置文件:
vim /etc/strongswan/ipsec.conf
配置文件常用设置说明:
config setup# 是否缓存证书吊销列表# <em>cachecrls = yes</em># 是否严格执行证书吊销规则# strictcrlpolicy=yes# 如果同一个用户在不同的设备上重复登录,yes 断开旧连接,创建新连接;no 保持旧连接,并发送通知;never 同 no,但不发送通知。uniqueids=no# 配置根证书,如果不使用证书吊销列表,可以不用这段。命名为 %default 所有配置节都会继承它# ca %default# 证书吊销列表 URL,可以是 LDAP,HTTP,或文件路径# crluri = <uri># 定义连接项,命名为 %default 所有连接都会继承它conn %default# 是否启用压缩,yes 表示如果支持压缩会启用compress = yes# 当意外断开后尝试的操作,hold,保持并重连直到超时dpdaction = hold# 意外断开后尝试重连时长dpddelay = 30s# 意外断开后超时时长,只对 IKEv1 起作用dpdtimeout = 60s# 闲置时长,超过后断开连接inactivity = 300s# 数据传输协议加密算法列表esp = aes256-sha256,aes256-sha1,3des-sha1!# 密钥交换协议加密算法列表ike = aes256-sha1-modp1024,aes128-sha1-modp1024,3des-sha1-modp1024!# 默认的密钥交换算法,ike 为自动,优先使用 IKEv2keyexchange = ike# 服务端公网 IP,可以是魔术字 %any,表示从本地 IP 地址表中取left = %any# 客户端 IP,同上right = %any# 指定服务端与客户端的 DNS,多个用“,”分隔leftdns = 8.8.8.8,8.8.4.4rightdns = 8.8.8.8,8.8.4.4# 服务端用于 ike 认证时使用的端口,默认为 500,如果使用了 nat 转发,则使用 4500# leftikeport = <port># 服务器端虚拟 IP 地址# leftsourceip = %config# 客户端虚拟 IP 段rightsourceip = 10.0.0.0/24# 服务器端子网,魔术字 0.0.0.0/0 。如果为客户端分配虚拟 IP 地址的话,那表示之后要做 iptables 转发,那么服务器端就必须是用魔术字leftsubnet = 0.0.0.0/0# rightsubnet = <ip subnet>[[<proto/port>]][,...]conn IKEv2-BASE# 服务器端根证书 DN 名称leftca = "C=CN, O=123si, CN=123si StrongSwan CA"# 服务器证书,可以是 PEM 或 DER 格式leftcert = server.cert.pem# 不指定客户端证书路径# rightcert = <path># 指定服务器证书的公钥leftsigkey = server.pub.pem# rightsigkey = <raw public key> | <path to public key># 是否发送服务器证书到客户端leftsendcert = always# 客户端不发送证书rightsendcert = never# 服务端认证方法,使用证书leftauth = pubkey# 客户端认证使用 EAP 扩展认证,貌似 eap-mschapv2 比较通用rightauth = eap-mschapv2# 服务端 ID,可以任意指定,默认为服务器证书的 subject,还可以是魔术字 %any,表示什么都行leftid = vpn.itnmg.net# 客户端 id,任意rightid = %any# ios, mac os, win7+, linuxconn IKEv2-EAPalso = IKEv2-BASE# 指定客户端 eap ideap_identity = %any# 不自动重置密钥rekey = no# 开启 IKE 消息分片fragmentation = yes# 当服务启动时,应该如何处理这个连接项。add 添加到连接表中。auto = add
我的配置:
# ipsec.conf - strongSwan IPsec configuration file# basic configurationconfig setup# strictcrlpolicy=yesuniqueids = never# Add connections here.# Sample VPN connections#conn sample-self-signed# leftsubnet=10.1.0.0/16# leftcert=selfCert.der# leftsendcert=never# right=192.168.0.2# rightsubnet=10.2.0.0/16# rightcert=peerCert.der# auto=start#conn sample-with-ca-cert# leftsubnet=10.1.0.0/16# leftcert=myCert.pem# right=192.168.0.2# rightsubnet=10.2.0.0/16# rightid="C=CH, O=Linux strongSwan CN=peer name"# auto=startconn %defaultcompress = yesesp = aes256-sha256,aes256-sha1,3des-sha1!ike = aes256-sha256-modp2048,aes256-sha1-modp2048,aes128-sha1-modp2048,3des-sha1-modp2048,aes256-sha256-modp1024,aes256-sha1-modp1024,aes128-sha1-modp1024,3des-sha1-modp1024!keyexchange = ikekeyingtries = 1leftdns = 8.8.8.8,8.8.4.4rightdns = 8.8.8.8,8.8.4.4conn IKEv2-BASE# 服务器端根证书 DN 名称leftca = "C=CN, O=123si, CN=123si StrongSwan CA"# 是否发送服务器证书到客户端leftsendcert = always# 客户端不发送证书rightsendcert = neverconn IKEv2-EAPleftca = "C=CN, O=123si, CN=123si StrongSwan CA"leftcert = server.cert.pemleftsendcert = alwaysrightsendcert = neverleftid = 48.85.166.86left = %anyright = %anyleftauth = pubkeyrightauth = eap-mschapv2leftfirewall = yesleftsubnet = 0.0.0.0/0rightsourceip = 10.1.0.0/16fragmentation = yesrekey = noeap_identity = %anyauto = add
2、修改 DNS 配置
strongSwan v5.1.2 之后,所有插件配置都分散在/etc/strongswan/strongswan.d/目录中。
编辑配置文件:
vim /etc/strongswan/strongswan.d/charon.conf
设置 Windows 公用 DNS,去掉dns1和dns2前面的井号(#)。
修改如下:
# Options for the charon IKE daemon.charon {# Accept unencrypted ID and HASH payloads in IKEv1 Main Mode.# accept_unencrypted_mainmode_messages = no# Maximum number of half-open IKE_SAs for a single peer IP.# block_threshold = 5# Whether Certificate Revocation Lists (CRLs) fetched via HTTP or LDAP# should be saved under a unique file name derived from the public key of# the Certification Authority (CA) to /etc/ipsec.d/crls (stroke) or# /etc/swanctl/x509crl (vici), respectively.# cache_crls = no# Whether relations in validated certificate chains should be cached in# memory.# cert_cache = yes# Send Cisco Unity vendor ID payload (IKEv1 only).# cisco_unity = no# Close the IKE_SA if setup of the CHILD_SA along with IKE_AUTH failed.# close_ike_on_child_failure = no# Number of half-open IKE_SAs that activate the cookie mechanism.# cookie_threshold = 10# Delete CHILD_SAs right after they got successfully rekeyed (IKEv1 only).# delete_rekeyed = no# Delay in seconds until inbound IPsec SAs are deleted after rekeyings# (IKEv2 only).# delete_rekeyed_delay = 5# Use ANSI X9.42 DH exponent size or optimum size matched to cryptographic# strength.# dh_exponent_ansi_x9_42 = yes# Use RTLD_NOW with dlopen when loading plugins and IMV/IMCs to reveal# missing symbols immediately.# dlopen_use_rtld_now = no# DNS server assigned to peer via configuration payload (CP).# Windows 公用 DNSdns1 = 8.8.8.8# DNS server assigned to peer via configuration payload (CP).# Windows 公用 DNSdns2 = 8.8.4.4# Enable Denial of Service protection using cookies and aggressiveness# checks.# dos_protection = yes# Compliance with the errata for RFC 4753.# ecp_x_coordinate_only = yes# Free objects during authentication (might conflict with plugins).# flush_auth_cfg = no# Whether to follow IKEv2 redirects (RFC 5685).# follow_redirects = yes# Maximum size (complete IP datagram size in bytes) of a sent IKE fragment# when using proprietary IKEv1 or standardized IKEv2 fragmentation, defaults# to 1280 (use 0 for address family specific default values, which uses a# lower value for IPv4). If specified this limit is used for both IPv4 and# IPv6.# fragment_size = 1280# Name of the group the daemon changes to after startup.# group =# Timeout in seconds for connecting IKE_SAs (also see IKE_SA_INIT DROPPING).# half_open_timeout = 30# Enable hash and URL support.# hash_and_url = no# Allow IKEv1 Aggressive Mode with pre-shared keys as responder.# i_dont_care_about_security_and_use_aggressive_mode_psk = no# Whether to ignore the traffic selectors from the kernel's acquire events# for IKEv2 connections (they are not used for IKEv1).# ignore_acquire_ts = no# A space-separated list of routing tables to be excluded from route# lookups.# ignore_routing_tables =# Maximum number of IKE_SAs that can be established at the same time before# new connection attempts are blocked.# ikesa_limit = 0# Number of exclusively locked segments in the hash table.# ikesa_table_segments = 1# Size of the IKE_SA hash table.# ikesa_table_size = 1# Whether to close IKE_SA if the only CHILD_SA closed due to inactivity.# inactivity_close_ike = no# Limit new connections based on the current number of half open IKE_SAs,# see IKE_SA_INIT DROPPING in strongswan.conf(5).# init_limit_half_open = 0# Limit new connections based on the number of queued jobs.# init_limit_job_load = 0# Causes charon daemon to ignore IKE initiation requests.# initiator_only = no# Install routes into a separate routing table for established IPsec# tunnels.# install_routes = yes# Install virtual IP addresses.# install_virtual_ip = yes# The name of the interface on which virtual IP addresses should be# installed.# install_virtual_ip_on =# Check daemon, libstrongswan and plugin integrity at startup.# integrity_test = no# A comma-separated list of network interfaces that should be ignored, if# interfaces_use is specified this option has no effect.# interfaces_ignore =# A comma-separated list of network interfaces that should be used by# charon. All other interfaces are ignored.# interfaces_use =# NAT keep alive interval.# keep_alive = 20s# Plugins to load in the IKE daemon charon.# load =# Determine plugins to load via each plugin's load option.# load_modular = no# Initiate IKEv2 reauthentication with a make-before-break scheme.# make_before_break = no# Maximum number of IKEv1 phase 2 exchanges per IKE_SA to keep state about# and track concurrently.# max_ikev1_exchanges = 3# Maximum packet size accepted by charon.# max_packet = 10000# Enable multiple authentication exchanges (RFC 4739).# multiple_authentication = yes# WINS servers assigned to peer via configuration payload (CP).# nbns1 =# WINS servers assigned to peer via configuration payload (CP).# nbns2 =# UDP port used locally. If set to 0 a random port will be allocated.# port = 500# UDP port used locally in case of NAT-T. If set to 0 a random port will be# allocated. Has to be different from charon.port, otherwise a random port# will be allocated.# port_nat_t = 4500# Whether to prefer updating SAs to the path with the best route.# prefer_best_path = no# Prefer locally configured proposals for IKE/IPsec over supplied ones as# responder (disabling this can avoid keying retries due to# INVALID_KE_PAYLOAD notifies).# prefer_configured_proposals = yes# By default public IPv6 addresses are preferred over temporary ones (RFC# 4941), to make connections more stable. Enable this option to reverse# this.# prefer_temporary_addrs = no# Process RTM_NEWROUTE and RTM_DELROUTE events.# process_route = yes# Delay in ms for receiving packets, to simulate larger RTT.# receive_delay = 0# Delay request messages.# receive_delay_request = yes# Delay response messages.# receive_delay_response = yes# Specific IKEv2 message type to delay, 0 for any.# receive_delay_type = 0# Size of the AH/ESP replay window, in packets.# replay_window = 32# Base to use for calculating exponential back off, see IKEv2 RETRANSMISSION# in strongswan.conf(5).# retransmit_base = 1.8# Maximum jitter in percent to apply randomly to calculated retransmission# timeout (0 to disable).# retransmit_jitter = 0# Upper limit in seconds for calculated retransmission timeout (0 to# disable).# retransmit_limit = 0# Timeout in seconds before sending first retransmit.# retransmit_timeout = 4.0# Number of times to retransmit a packet before giving up.# retransmit_tries = 5# Interval in seconds to use when retrying to initiate an IKE_SA (e.g. if# DNS resolution failed), 0 to disable retries.# retry_initiate_interval = 0# Initiate CHILD_SA within existing IKE_SAs (always enabled for IKEv1).# reuse_ikesa = yes# Numerical routing table to install routes to.# routing_table =# Priority of the routing table.# routing_table_prio =# Whether to use RSA with PSS padding instead of PKCS#1 padding by default.# rsa_pss = no# Delay in ms for sending packets, to simulate larger RTT.# send_delay = 0# Delay request messages.# send_delay_request = yes# Delay response messages.# send_delay_response = yes# Specific IKEv2 message type to delay, 0 for any.# send_delay_type = 0# Send strongSwan vendor ID payload# send_vendor_id = no# Whether to enable Signature Authentication as per RFC 7427.# signature_authentication = yes# Whether to enable constraints against IKEv2 signature schemes.# signature_authentication_constraints = yes# The upper limit for SPIs requested from the kernel for IPsec SAs.# spi_max = 0xcfffffff# The lower limit for SPIs requested from the kernel for IPsec SAs.# spi_min = 0xc0000000# Number of worker threads in charon.# threads = 16# Name of the user the daemon changes to after startup.# user =crypto_test {# Benchmark crypto algorithms and order them by efficiency.# bench = no# Buffer size used for crypto benchmark.# bench_size = 1024# Time in ms during which crypto algorithm performance is measured.# bench_time = 50# Test crypto algorithms during registration (requires test vectors# provided by the test-vectors plugin).# on_add = no# Test crypto algorithms on each crypto primitive instantiation.# on_create = no# Strictly require at least one test vector to enable an algorithm.# required = no# Whether to test RNG with TRUE quality; requires a lot of entropy.# rng_true = no}host_resolver {# Maximum number of concurrent resolver threads (they are terminated if# unused).# max_threads = 3# Minimum number of resolver threads to keep around.# min_threads = 0}leak_detective {# Includes source file names and line numbers in leak detective output.# detailed = yes# Threshold in bytes for leaks to be reported (0 to report all).# usage_threshold = 10240# Threshold in number of allocations for leaks to be reported (0 to# report all).# usage_threshold_count = 0}processor {# Section to configure the number of reserved threads per priority class# see JOB PRIORITY MANAGEMENT in strongswan.conf(5).priority_threads {}}# Section containing a list of scripts (name = path) that are executed when# the daemon is started.start-scripts {}# Section containing a list of scripts (name = path) that are executed when# the daemon is terminated.stop-scripts {}tls {# List of TLS encryption ciphers.# cipher =# List of TLS key exchange methods.# key_exchange =# List of TLS MAC algorithms.# mac =# List of TLS cipher suites.# suites =}x509 {# Discard certificates with unsupported or unknown critical extensions.# enforce_critical = yes}}
3、配置用户名与密码
编辑配置文件:
vim /etc/strongswan/ipsec.secrets
添加用户名和密码:
# ipsec.secrets - strongSwan IPsec secrets file# 使用证书验证时的服务器端私钥# 格式 : RSA <private key file> [ <passphrase> | %prompt ]: RSA server.key.pem# 使用预设加密密钥, 越长越好# 格式 [ <id selectors> ] : PSK <secret>%any %any : PSK "abcdef123456"# EAP 方式, 格式同 psk 相同UserName1 %any : EAP "UserPassword1"UserName2 %any : EAP "UserPassword2"# XAUTH 方式, 只适用于 IKEv1# 格式 [ <servername> ] <username> : XAUTH "<password>"UserName1 %any : XAUTH "UserPassword1"UserName2 %any : XAUTH "UserPassword2"
4、开启内核转发
编辑系统配置文件:
vim /etc/sysctl.conf
在末尾处,添加如下配置项:
net.ipv4.ip_forward = 1net.ipv6.conf.all.forwarding = 1
或者,执行下面命令添加到系统配置文件。
echo "net.ipv4.ip_forward = 1" >> /etc/sysctl.confecho "net.ipv6.conf.all.forwarding = 1" >> /etc/sysctl.conf
最后重新加载系统参数,使上面的配置生效,执行命令:
sysctl -p
五、配置防火墙
配置 CentOS 7 系统默认防火墙 FirewallD。
注意,以下命令没有指定--zone=public参数,都是针对默认区域public。
1、为区域添加服务
firewall-cmd --permanent --add-service="ipsec"
2、允许 AH 和 ESP 身份验证协议和加密协议通过防火墙
# ESP (the encrypted data packets)firewall-cmd --permanent --add-rich-rule='rule protocol value="esp" accept'# AH (authenticated headers)firewall-cmd --permanent --add-rich-rule='rule protocol value="ah" accept'
3、开放 500 和 4500 端口
# IKE (security associations)firewall-cmd --permanent --add-port=500/udp# IKE NAT Traversal (IPsec between natted devices)firewall-cmd --permanent --add-port=4500/udp
4、启用 IP 伪装
firewall-cmd --permanent --add-rich-rule='rule family="ipv4" source address="10.1.0.0/16" masquerade'
5、添加 nat 转发
firewall-cmd --permanen --add-rich-rule='rule family="ipv4" source address="10.1.0.0/16" forward-port port="4500" protocol="udp" to-port="4500"'firewall-cmd --permanen --add-rich-rule='rule family="ipv4" source address="10.1.0.0/16" forward-port port="500" protocol="udp" to-port="500"'
6、重新加载防火墙配置
firewall-cmd --reload
7、显示所有公共区域(public)
firewall-cmd --list-all
查看上面命令执行结果。
六、strongSwan 服务操作
1、使用 strongswan 自身的命令
# 停止服务strongswan stop# 查看是否连接了客户端strongswan status# 查看命令帮助strongswan --help
2、使用 systemctl 命令
# 设置开机启动 strongswan 服务systemctl enable strongswan# 启动服务systemctl start strongswan# 停止服务systemctl stop strongswan# 重启服务systemctl restart strongswan# 查看服务状态systemctl status strongswan
注意,如果使用strongswan restart命令重启 strongSwan 后,再用systemctl status strongswan命令得不到正确的运行状态。
至此,服务端配置已完成。
七、客户端配置
IOS 系统
先导入 CA 证书,将之前创建的ca.cert.pem用 FTP 导出,写邮件以附件的方式发到邮箱, 在 IOS 浏览器登录邮箱,下载附件,安装 CA 证书。
1、使用 IKEv2 + EAP 认证
找到手机上“设置->VPN->添加配置”,选 IKEv2 。
- 描述:随便填
- 服务器:填 URL 或 IP
- 远程 ID:
ipsec.conf中的leftid - 用户鉴定:用户名
- 用户名:EAP 项用户名
- 密码:EAP 项密码
2、使用 IKEv2 + 客户端证书 认证
把之前的 .p12 证书(里面包含 CA 证书)发到邮箱在手机上打开。导入到手机(此时需要之前设置的证书密码)。
找到手机上“设置->VPN->添加配置’,选 IKEv2 。
- 描述:随便填
- 服务器:填 URL 或 IP
- 远程ID:
ipsec.conf中的leftid - 用户鉴定:证书
- 证书:选择安装完的客户端证书
3、使用 IKEv2 + 预设密钥 认证
找到手机上“设置->VPN->添加配置”,选 IKEv2 。
- 描述:随便填
- 服务器:填 URL 或 IP
- 远程ID:
ipsec.conf中的leftid - 用户鉴定:无
- 使用证书:关
- 密钥:PSK 项密钥
Windows 10
导入证书:
- 将 CA 根证书
ca.cert.pem重命名为ca.cert.crt; - 双击
ca.cert.crt开始安装证书; - 点击安装证书;
- “存储位置”选择“本地计算机”,下一步;
- 选择“将所有的证书都放入下列存储区”,点浏览,选择“受信任的根证书颁发机构”,确定,下一步,完成;
建立连接:
- “控制面板”-“网络和共享中心”-“设置新的连接或网络”-“连接到工作区”-“使用我的 Internet 连接”;
- Internet 地址写服务器 IP 或 URL;
- 描述随便写;
- 用户名密码写之前配置的 EAP 的那个;
- 确定;
- 转到 控制面板网络和 Internet 网络连接;
- 在新建的 VPN 连接上右键属性然后切换到“安全”选项卡;
- VPN 类型选 IKEv2 ;
- 数据加密选“需要加密”;
- 身份认证这里需要说一下,如果想要使用 EAP 认证的话就选择“Microsoft : 安全密码(EAP-MSCHAP v2)”;想要使用私人证书认证的话就选择“使用计算机证书”;
- 再切换到“网络”选项卡,双击“Internet 协议版本 4”以打开属性窗口,这里说一下,如果你使用的是老版本的 Win10,可能会打不开属性窗口,这是已知的 Bug,升级最新版本即可解决;
- 点击“高级”按钮,勾选“在远程网络上使用默认网关”,确定退出;
Windows 7 导入证书略有不同
- 开始菜单搜索“cmd”,打开后输入
MMC(Microsoft 管理控制台); - “文件”-“添加/删除管理单元”,添加“证书”单元;
- 证书单元的弹出窗口中一定要选“计算机账户”,之后选“本地计算机”,确定;
- 在左边的“控制台根节点”下选择“证书”-“受信任的根证书颁发机构”-“证书”,右键“所有任务”-“导入”打开证书导入窗口;
- 选择 CA 证书
ca.cert.crt导入即可;
注意,千万不要双击 .p12 证书导入!因为那样会导入到当前用户而不是本机计算机中。
八、可能遇到的问题
关于 Windows 10 系统中 VPN 能正常连接,但不能打开网页的情况。
这与“VPN 连接”属性中的“接口跃点数”设置有关。该设置用于设置网络接口的优先级,使用 cmd 执行命令
route print查看路由表,知道其他接口的跃点数后,我们只要将“VPN 连接”的“接口跃点数”设置低于它们就可以了。设置好后,网络请求会优先使用“VPN 连接”。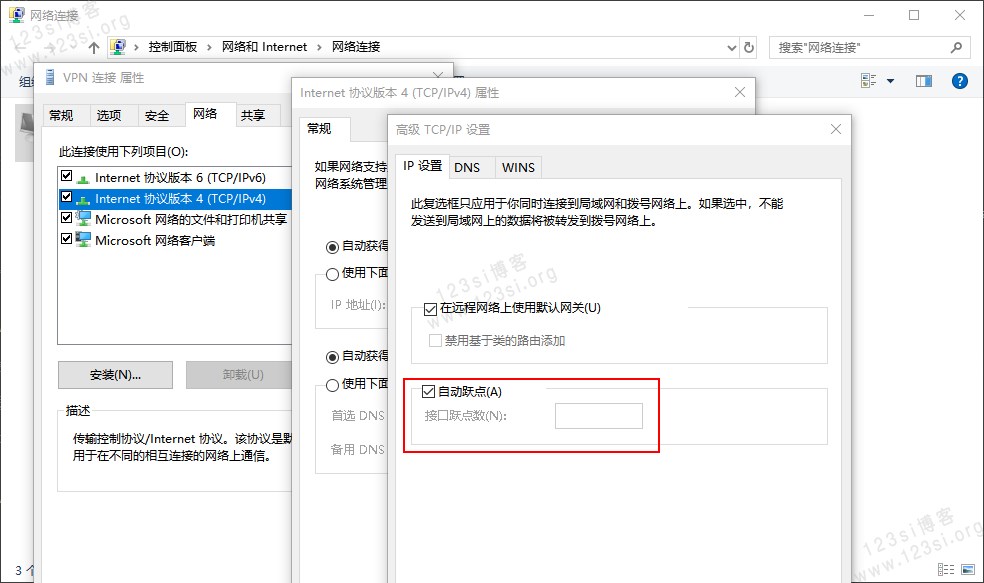
图为:接口跃点数的设置。
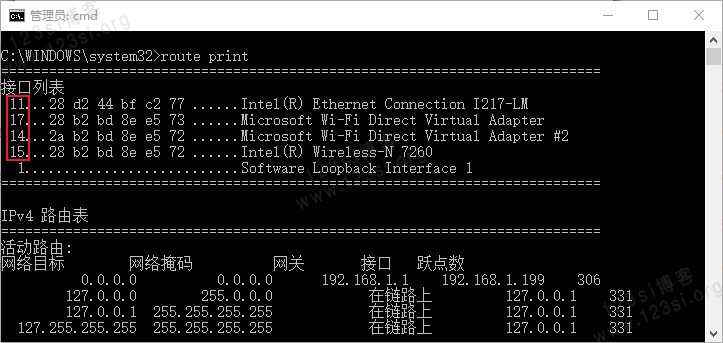
图为:
route print命令执行结果。图中“接口列表”第一列,用红色圈出的部分为跃点数,将“VPN 连接”的“接口跃点数”设置为 10 即可。
九、参考文献
- strongSwan - 官网
- IPSEC VPN on Centos 7 with StrongSwan
- CentOS 7 配置 IPSec-IKEv2 VPN, 适用于 ios, mac os, windows, linux.
- 在阿里云 CentOS 7上使用strongswan搭建IKEv2 VPN
- 一键搭建适用于Ubuntu/CentOS的IKEV2/L2TP的VPN
(完)